
Cyber, privacy & resilience
Data Protection and Compliance

Navigating challenges together: we will get you there
Even with security controls in place, your privacy challenges might not be addressed, as security and privacy often overlap but also involve distinct risks. Success lies in the collaboration of cybersecurity professionals, data protection experts and privacy engineers; where threats are monitored, controls are implemented, regulatory requirements are met, and the pillars of privacy are embedded into the design of systems and processes.
At PwC Belgium, we believe a holistic approach to privacy and security is essential. Our team of professionals combines technical and academic backgrounds: legal experts, privacy engineers, ethical hackers, training and change managers, policy specialists, and security architects. Together they will enhance and streamline your security while ensuring compliance with applicable privacy and data protection laws, across departments and country borders.

The roadmap to compliance
Embark on your journey to privacy maturity with [our tailored] roadmap, guiding you through the essential steps to achieve data protection compliance. Whether you need the full journey or just select steps, our approach adapts to your specific needs, empowering your business to build trust, enhance your brand, and drive growth through robust privacy strategies.

Step 1: Stakeholder Awareness
Purpose: To ensure stakeholders understand the importance of GDPR compliance and the specific challenges it entails, supporting informed decision making.
Outcome: Informed and engaged stakeholders who are aware of their roles and responsibilities regarding data protection.

Step 2: Gaining Data and Data Processing Oversight
Purpose: To govern processing activities and understand data flows during their life cycles. This will improve control over security and privacy investments, data subject requests, data breach response, and other essential areas.
Outcome: A data inventory and map that facilitates transparency, audits, and identifies gaps and changes, and ensures data management in the Records of Processing Activities to support accountability.

Step 3: Gap Analysis
Purpose: To assess current activities, policies and procedures against GDPR requirements.
Outcome: Identification of data protection and compliance gaps in oversight, transparency, controls, or accountability.
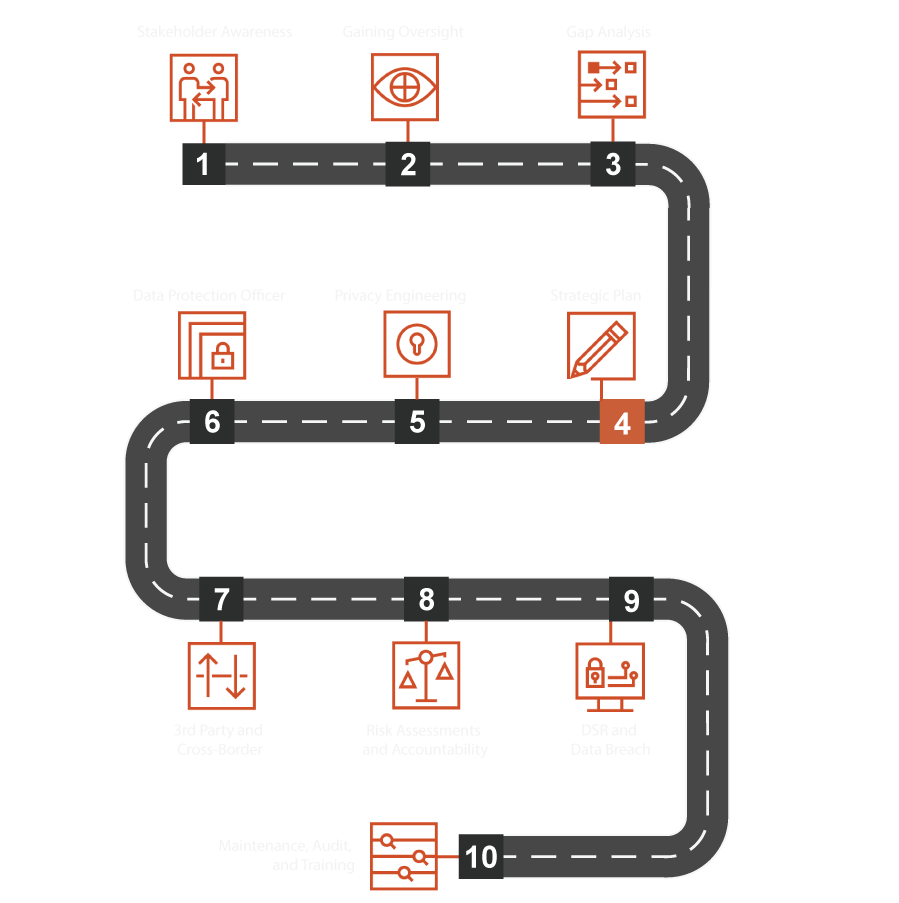
Step 4: Strategic Plan
Purpose: To develop a strategic plan to address the gaps identified in the gap analysis.
Outcome: A detailed roadmap outlining actions, timelines and responsibilities to achieve GDPR compliance.

Step 5: Privacy Engineering
Purpose: To incorporate privacy and data protection measures into the design of new features, processes, and systems to protect user data, foster trust and reduce the likelihood of privacy issues.
Outcome: Development of robust and privacy-friendly processes and systems.

Step 6: Data Protection Officer
Purpose: To assess the role and position of a DPO within the organization and establish a privacy champions network.
Outcome: A designated DPO or equivalent, ensuring continuous monitoring of data protection practices, supported by a network of privacy champions.

Step 7: Third Party and Cross-Border Data Management
Purpose: To ensure data transfers to third-parties and cross-border are secure and compliant.
Outcome: Establishment of a practical management framework to guarantee compliance with third-party and cross-border data transfer regulations.

Step 8: Risk assessments and accountability
Purpose: To implement tools, platforms, and processes to document and demonstrate compliance with GDPR, incorporating DPIAs for high-risk processing activities, and to conduct assessments for processing activities to mitigate high risks to the security of data processing and the rights and freedoms of data subjects.
Outcome: A comprehensive accountability framework that provides clear evidence of compliance and detailed DPIAs.

Step 9: Data Subject Right Requests and Data Breaches
Purpose: To develop and embed policies and procedures to handle data subject right requests and data breaches.
Outcome: Procedures ensuring that data subjects can exercise their rights and that data breaches are managed and reported according to GDPR and local data protection authority requirements.

Step 10: Maintenance, Audit, and Training
Purpose: To ensure ongoing compliance through regular audits, updates to policies and procedures, and continuous training.
Outcome: An organizational culture of data protection and privacy, maintained through continuous improvement and awareness.
Contact us













