1. Verifiable credentials and Self-sovereign Identity (SSI)
This is one of the major trends these past two years. Both companies and governments are investing heavily into the concepts of verifiable credentials and self-sovereign identity. Why? Because it holds potential for securely storing and managing official documents such as university degrees, digital driver’s licences, passports, identity cards, and more. These concepts would make us digital custodians of our credentials, enabling innovative applications such as electronic car locks that only unlock with a valid digital driver's licence. Besides, a shift lik that would eliminate the need to produce physical copies of documents like university degrees, thereby streamlining processes and reducing administrative burdens. However, this architecture of verifiable credentials and self-sovereign identity is entirely based on the concept of decentralised identity. In other words, it calls for unique identifiers and cryptographic signatures that individuals own independently of any central authority.
2. Policy-Based Access Controls (PBAC)
PBAC isn’t a new concept or trend: In fact it has been around at least conceptually since the 1990’s. But it’s only recently that we’ve been seeing vendors and organisations adopting it into their products or ways of working. A major reason for this adoption may be the ease of use and the amalgamation of favourable aspects in both Role-Based Access Control (RBAC) and Attribute-based access control (ABAC). For example, PBAC offers finer-grained access control than RBAC, enables the integration of ABAC criteria with RBAC, and can even incorporate risk levels from RAdAC. Many companies have already implemented either a RBAC or ABAC system into their solutions. However a PBAC system can elevate such solutions to the next level. Not only does it offer relative ease of use, but it can also be configured in human-readable language. This reduces the administrative burden of maintenance or administration personnel.
3. Risk Adaptive Access Controls (RAdAC)
Risk adaptive Access Controls, or RAdAC, build upon a relatively simple premise: considering all possible variables in a login attempt and assigning a level of risk to it. Vendors are increasingly incorporating RAdAC into their available options to enforce multi-factor authentication journeys or even to outright block access if the risk is deemed too high. Moreover, It can be utilised in conjunction with PBAC exception rules or other access control philosophies. The potential of RAdAC is significant, particularly in today’s climate of heightened cybersecurity threats, where users often represent the weakest link in the security chain. By providing users with dynamic risk levels and triggering multi-factor authentication or lock-out measures only when necessary, potential MFA fatigue experienced by users can be reduced. However, transitioning to a passwordless approach remains the most effective strategy for eliminating fatigue entirely.
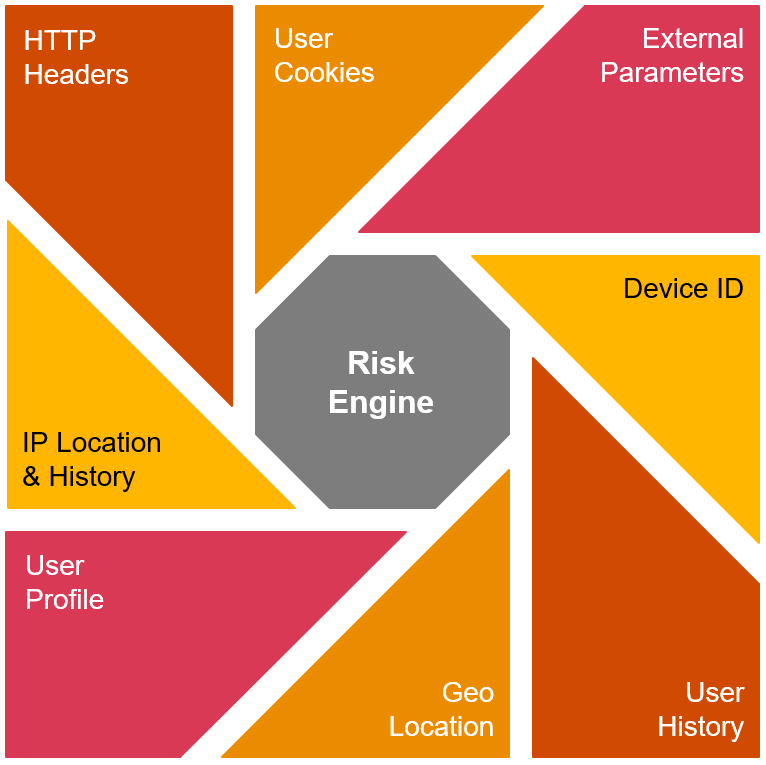
4. The Unified Identity Security movement
Over the past few years, various vendors have transitioned towards a more integrated or unified security approach for their Identity and Access Management (IAM) tools. This shift is hoped to streamline processes by reducing reliance on multiple vendors and consolidating dashboards into a centralised overview. Administration of all product facets would then occur in one centralised location, eliminating the need to access specific endpoints for Identity and Access Management tasks. Examples include the ForgeRock stream in Ping, Okta dashboarding, Cyberark and OneIdentity/OneLogin, all of which have adopted a unified look and approach to Identity Security. CyberArk and OneIdentity have even gone a step further by integrating their Privileged Access Management (PAM) services directly within their platforms.
In this movement towards a more integrated approach, many vendors like Delinea, CyberArk and Okta have used mergers and acquisitions to further grow their offering to a more complete picture. For example Delinea recently acquired two new companies boasting distinctly different product portfolios, a Cloud infrastructure Entitlements Manager (CIEM) and an Identity Threat Detection & Response (ITDR) tooling suite. They’ve also incorporated a Privileged Identity Governance and Administration (IGA) solution featuring machine learning AI.
Another interesting example is that of CyberArk, who have signed a definitive acquisition agreement to acquire a Machine Identity Management leader. These are just a few of many cases where we see vendors striving towards a complete one-stop solution.
5. Identity Threat Detection & Response (ITDR)
Many within the cyber world are undoubtedly familiar with what XDR and EDR stand for by now, along with their respective functionalities. But another niche detection system has recently emerged: ITDR or Identity Threat Detection & Response. Typically integrated into a unified identity security platform, ITDR can promptly respond to identity-related threats such as phishing attacks, MFA fatigue attacks, or malicious user behaviour. The only downside of this solution is its vendor-specific nature, especially since many vendors have yet to implement it. Notable pioneer examples include Cyberark, Microsoft, SentinelOne, and Crowdstrike. Some of these vendors’ products offer the ability to manage multiple platforms, such as SentinelOne and Crowdstrike. Conversely, others like Okta prioritise Identity Threat Protection (ITP) capabilities over general ITDR functionalities. In the case of Okta, these are reinforced by Okta A.I.
6. A.I. within Digital Identity
A.I. integration within digital identity products is not a novel concept. Over the past five years, numerous vendors have integrated machine learning A.I. into their products. But the recent surge in generative A.I. has yet to significantly impact digital identity itself, save for heightened risk of account takeovers. This trend can be interpreted in two ways. On one hand, generative A.I.’s main purpose is to inspire ideas and streamline work processes under supervision, presenting opportunities for individuals and organisations seeking to boost their productivity. On the other hand, the ascent of generative A.I. also introduces heightened threats to digital identity systems. As deep fakes become more prevalent, identity verification software must enhance its reliability and resilience to counter these threats. Consequently, this often results in an A.I. versus A.I. competition, given that most identity verification tools on the market rely on machine learning AI to validate faces in images and real-life scenarios.
Conclusion
Whilst we’ve only highlighted a selection of trends, there are certainly more still underway, such as the buildup of passwordless authentication. Many vendors already offer passwordless authentication with FIDO2 compliant integrations. This means they can tie in seamlessly with the likes of Windows Hello, Yubi key’s or others. Most also offer a more basic approach with X509 certificates bound to your devices. However, passwordless authentication is still not that widely adopted within corporations where they still focus on passwords coupled with MFA (Multi-factor authentication). However going fully passwordless has many advantages, as it decreases the attack surface. A nice example in the CIAM world would be Github where it is being pushed as the main authentication mechanism.
That being said, Consumer or Customer IAM will progress at a different pace than Workforce IAM due to the inherent differences in user types. One movement you're unlikely to see in Workforce IAM but is prevalent in CIAM is self-sovereign identity, since in Workforce IAM the owner of your data and credentials is typically the company you are employed by. Conversely, a trend you would observe in Workforce IAM and not in CIAM is Policy-based access control. But there are some evident trends across both IAM streams as well, such as AI, RAdAC, and consolidation moves. ITDR remains primarily associated with Workforce IAM, as the risks posed to enterprises by compromised enterprise accounts are significantly higher than those posed by compromised customer accounts.
In conclusion, the Digital Identity world is still pushing strongly forward, with new trends and movements on the horizon. For now the main driving force behind this push is the strong adoption of a complete zero trust architectural design principle across companies for their workforce system. Single self controlled digital identity is the driving force behind innovation in CIAM. So while there are indeed two different driving forces, the collaboration and cross-pollination of ideas between Workforce IAM and CIAM have the potential to drive significant advancements in the Digital Identity field as a whole.
Contact us











